Cyber Criminals – Lets make it difficult for them
Cyber Criminals – Lets make it difficult for them
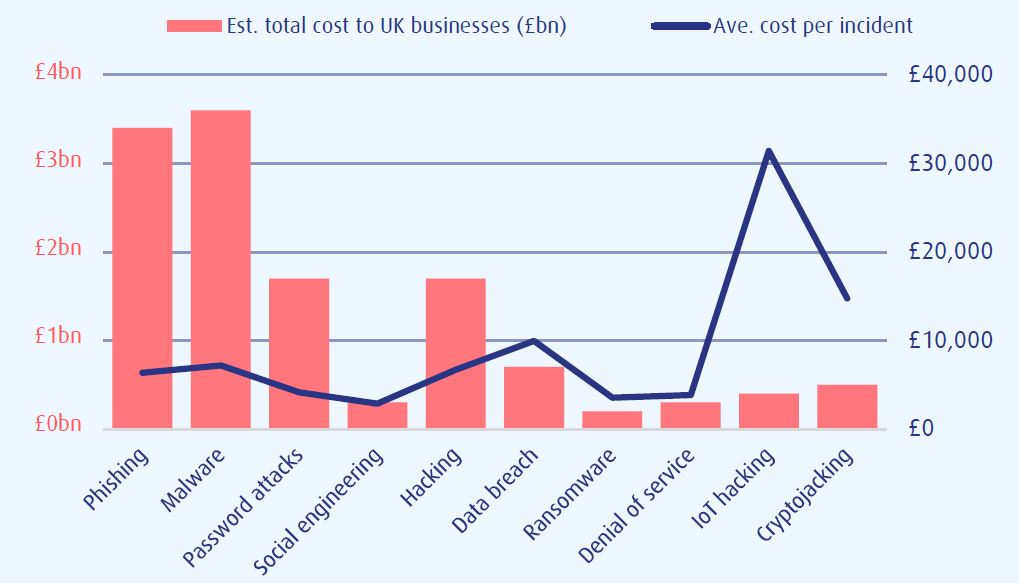
Cyber Criminals will take advantage of weakness in a companies IT infrastructure to attain information, money or media. This concerns us here at CCSW; more than you know! We have therefore put together a collection of tips to help you avoid getting caught out: