Cyber Criminals – Lets make it difficult for them

Cyber Criminals will take advantage of weakness in a companies IT infrastructure to attain information, money or media. This concerns us here at CCSW; more than you know! We have therefore put together a collection of tips to help you avoid getting caught out:

Security Checklist
- Email address from within the organisation. Always carry out an exact check that it is from an email address you recognise. Some Cyber Criminals like to register domain names very close to a companies actual domain name. It looks the same without closer inspection.
- There isn’t an email signature on the email. If there is, check for signs that it’s up-to-date, someone may of copied and pasted it from an actual email.
- If a mobile number is being requested, it’s likely they are trying to get hold of your 2FA (2 Factor authentication) code.
- The writing style – does this individual normally write emails like this?
- If someone attaches a file which then asks you to click a link to download an invoice / receipt etc. be very careful as it could be a fake Microsoft logon form trying to steal your details.
- Be careful with any links to dropbox / sharepoint especially if the system is asking you to logon to access the file.
- The email does not use your proper name, but uses a non-specific greeting like “dear customer”.
- A sense of urgency; for example, a threat that unless you act immediately your account may be closed.
- A prominent website link. These can be forged or seem very similar to the proper address, but even a single character difference means a different website.
- A request for personal information such as user name, password or bank details.
- If someone sends you updated payment information, this could be an individual or a company; always follow processes to confirm the change verbally.
- The email contains speling and grammticl errors.
- You weren’t expecting to get an email from the company that appears to have sent it.
- The entire text of the email is contained within an image rather than the usual text format.
- The image contains an embedded hyperlink to a bogus site.
- A message to say that your mailbox has run out of space.
- If ever in any doubt, please ring the person who has sent the email to check that they have actually sent it.
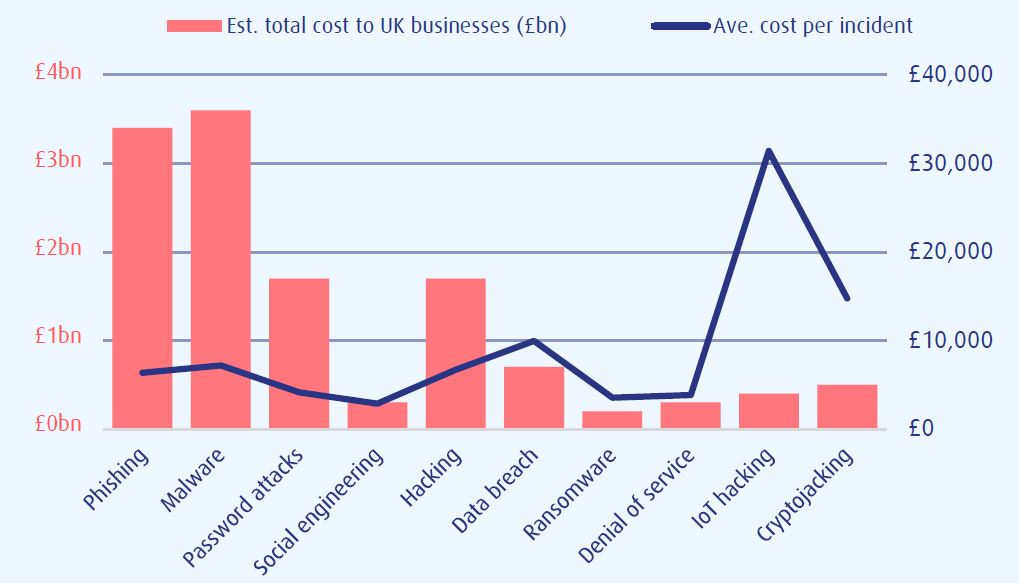
Cost – UK Businesses in 2019